Looking at Tenable?
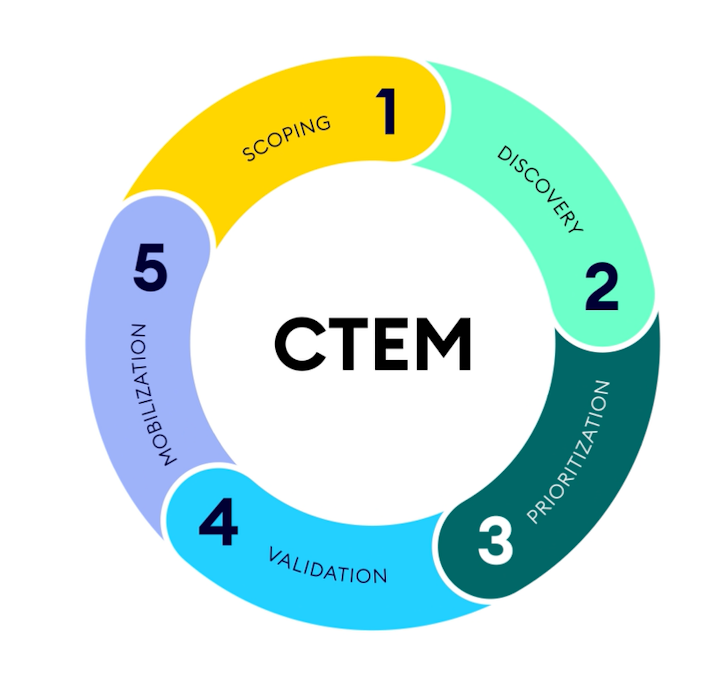
Move Beyond Vulnerability Management with Continuous Exposure Management
XM Cyber transforms Vulnerability Management through a threat-led Continuous Threat Exposure Management (CTEM) approach, delivering high-fidelity CVE discovery and dynamic risk mapping to assess true business threats.