Still relying on traditional Risk Based Vulnerability Management?
Move from RBVM to Continuous Threat Exposure Management (CTEM)
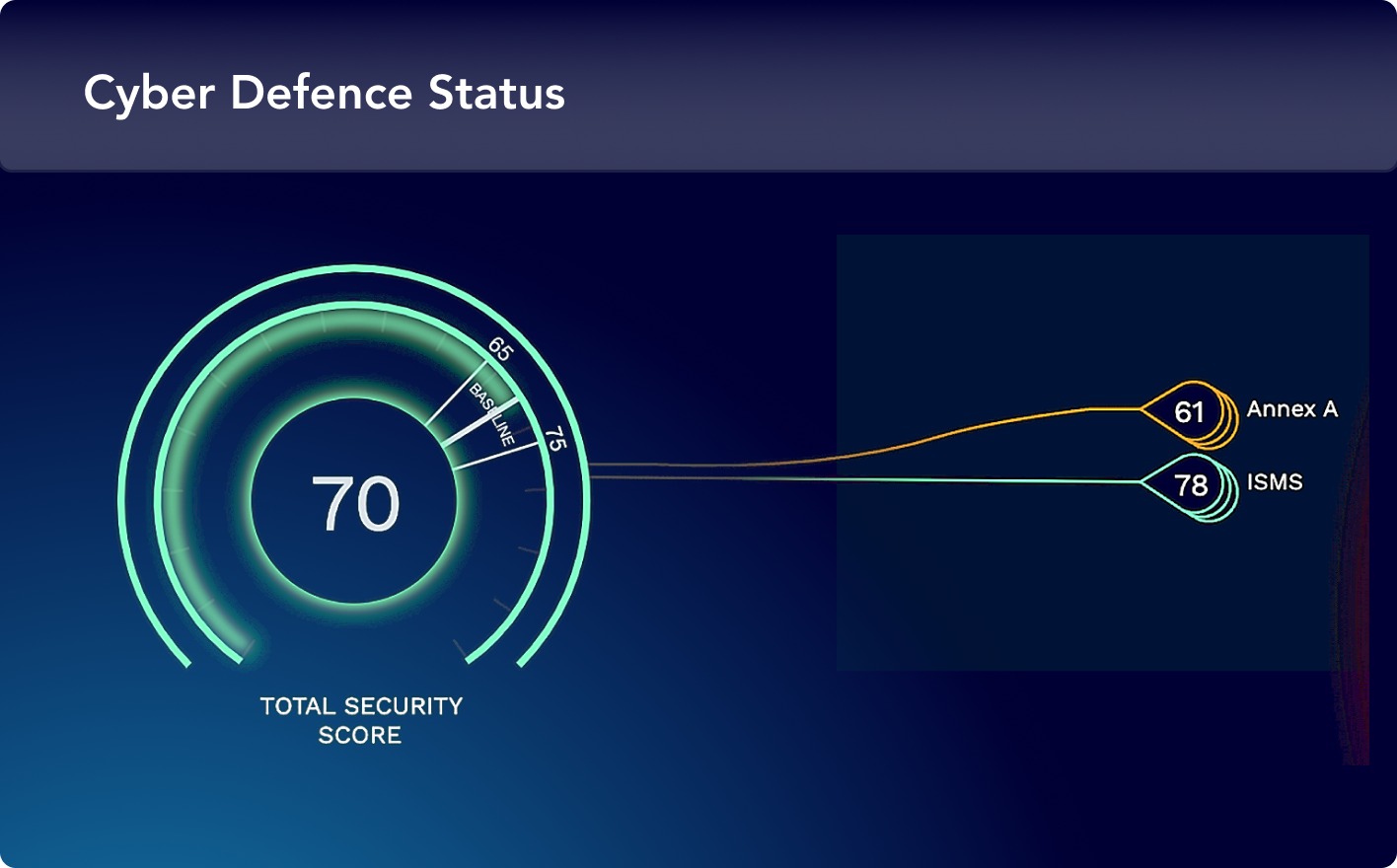
Prioritizing vulnerabilities with RBVM isn't enough - siloed risk scores still leave you exposed to the most critical attack paths.
The XM Cyber platform moves beyond theory and shows you how to dismantle the real-world risks:
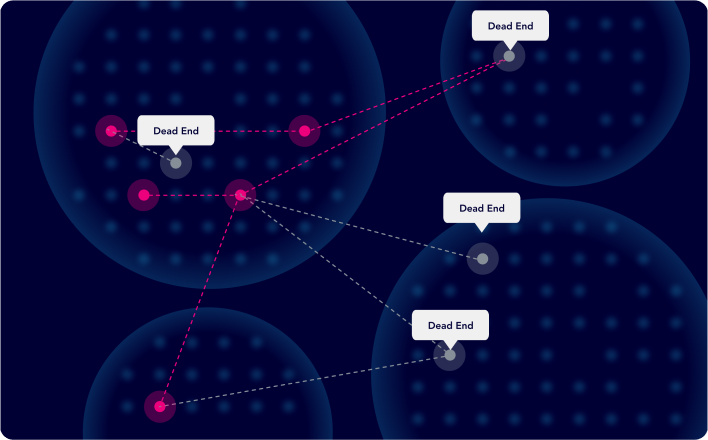
- Continuously maps the attack paths an adversary could take to your crown jewels.
- Pinpoints the "choke points" where a single remediation can sever multiple threats.
- Shows you exactly how vulnerabilities, identity exposures, and misconfigurations connect.
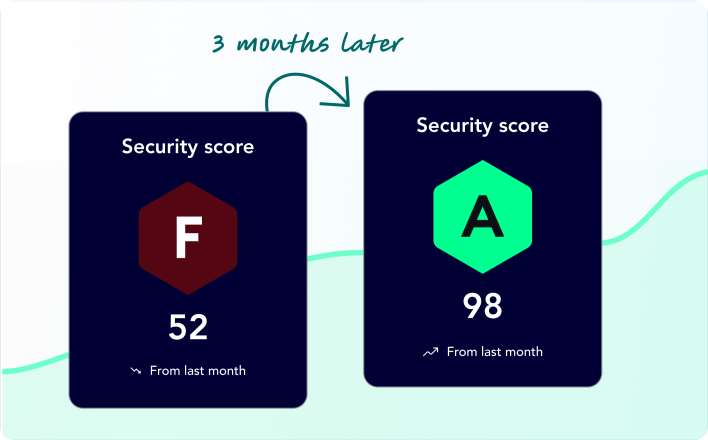
Focus on fixing what matters and make your existing RBVM strategy truly effective.