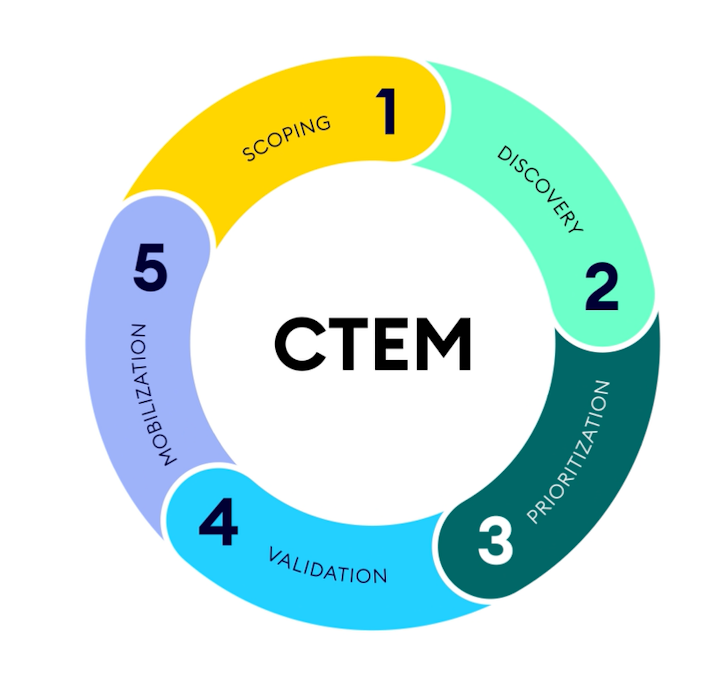
Looking at Exposure Management?
The Exposure Management Platform That Helps You Focus on the Risks That Matter
Traditional Vulnerability Management is no longer enough — scanning and prioritization alone can’t keep pace.
XM Cyber's Exposure Management platform:
- Continuously maps attack paths
- Identifies exploitable risks
- Shows you exactly how exposures interconnect to compromise your critical assets
Focus on what truly matters — reducing real-world exposures.










.gif)