The Cloud Security Disconnect:
Bridging the Gap Between Processes, Tools and Teams from On-prem to the Cloud
You can’t protect the cloud without protecting your on-prem. In today's rapidly evolving digital landscape, organizations are increasingly adopting cloud infrastructure to gain agility, scalability, and cost efficiencies. However, this shift to the cloud introduces a significant challenge: a disconnect between different people, processes and technologies that are opening up risk. Many organizations struggle with the following pain points.
| Limited Visibility: | Compliance Risks: | Inefficient Remediation: |
| Insufficient visibility in cloud environments leads to disconnected processes across on-prem and cloud creating inefficiencies for security teams to manage exposures through a single pane of glass. | Organizations face regulatory compliance challenges when operating in hybrid environments. Disparate solutions create risk from disconnected tools unable to provide a holistic understanding of the security posture across on-prem and cloud infrastructure. | IT and Security teams separately tackling security issues in the cloud or on-prem leads to fragmented remediation approaches, causing redundant efforts, resource wastage, and overall inefficiency in security. Organizations require an intelligent approach to identify and prioritize remediation efforts across their hybrid environments. |

Unifying Cloud Security with XM Cyber's Exposure Management Platform
Ultra-efficient remediation using attack graphs
.gif?width=1000&height=668&name=Attack%20Path%20Choke%20Point%20GIF%20(1).gif)
- Uncover vulnerabilities, privileged access abuse, and data exfiltration attempts originating from within your organization. Detect and neutralize insider threats proactively.
- Identify and mitigate risks associated with publicly accessible VMs. Visualize attack vectors and promptly apply security measures to safeguard your VMs.
- Swiftly address security breaches caused by stolen credentials. Simulate attack paths to identify impacted systems and take immediate remedial actions.
Safeguard Cloud environments from compromised users and credentials
- Proactively identify and mitigate exposures that would lead to unauthorized escalation of privileges.
- Understand which users cause disproportionate risk to cloud infrastructure.
- Identify which measures can efficiently reduce risk that compromised users pose.
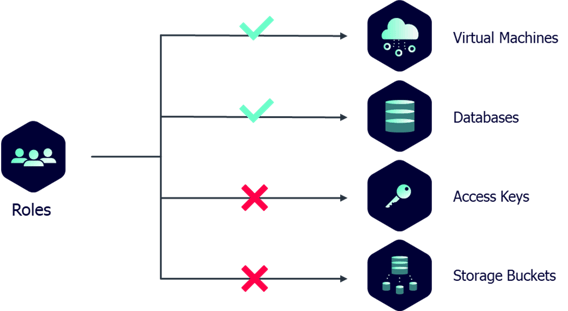
Gain control and reduce risks by removing unused or excessive permissions.
- Safeguard critical assets by managing excessive permissions.
- Optimize security by evaluating built-in and service accounts.
- Remove unnecessary or unused/shadow admins.
- Protect your critical assets from compromise by proactively addressing vulnerabilities associated with various entities, ensuring the security of your valuable resources.
Mitigate third-party risks and protect your cloud environment
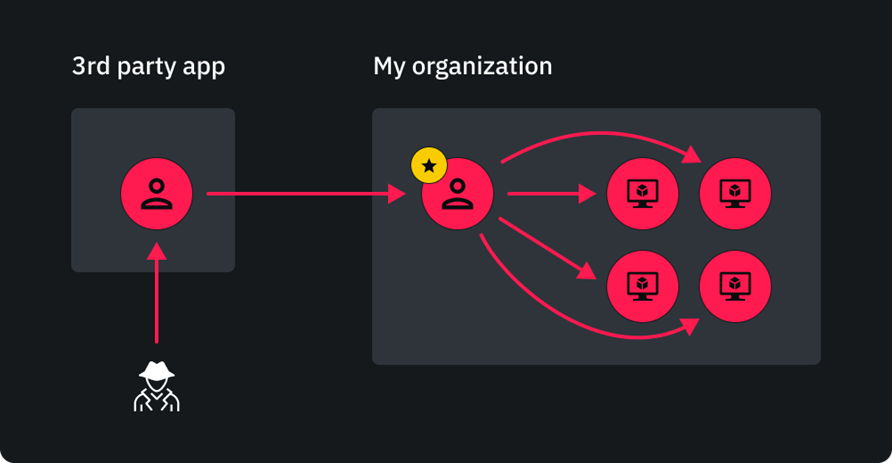
- Strengthen security and prevent compromise of virtual machines.
- Ensure robust security by removing unused external users to prevent unauthorized access.
- Protect your tenant from unauthorized takeovers by carefully managing user privileges and limiting high-level access.
Cloud Attack Path Modelling
- See how attackers can compromise cloud environments by moving laterally from traditional environments.
- Don’t treat cloud like another silo - avoid the Big Cloud Security Disconnect!
- Proactively manage risk to cloud assets during digital transformation.
