Looking at Automated Security Validation?
See Why XM Cyber Leads in Automated Security Validation
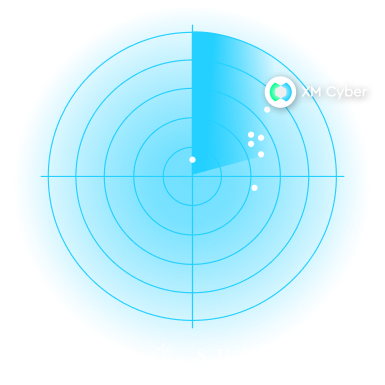
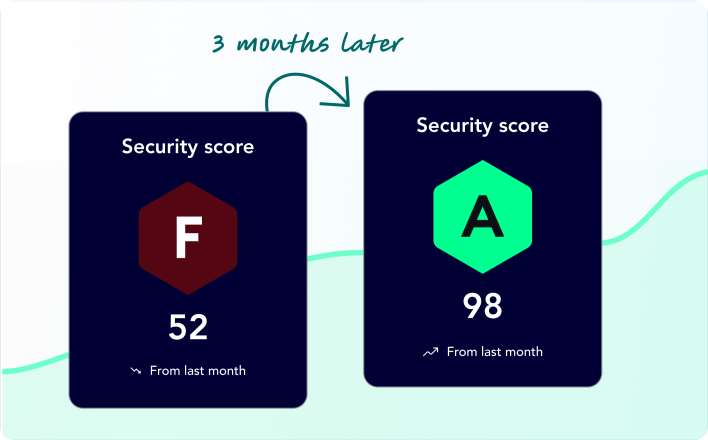
XM Cyber has been recognized as the undisputed leader in the 2024 Automated Security Validation (ASV) Radar by Frost & Sullivan.
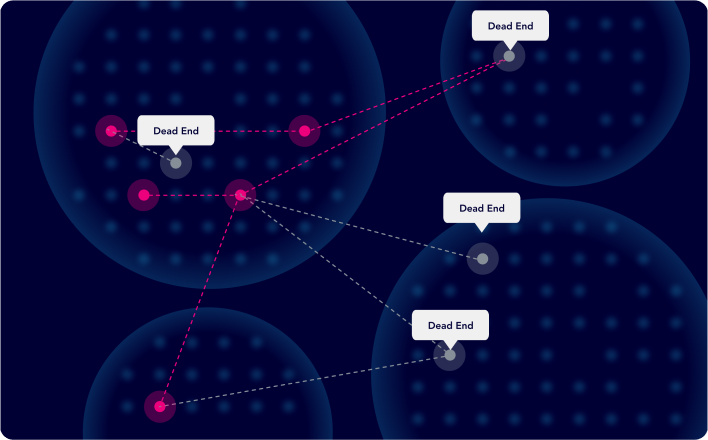
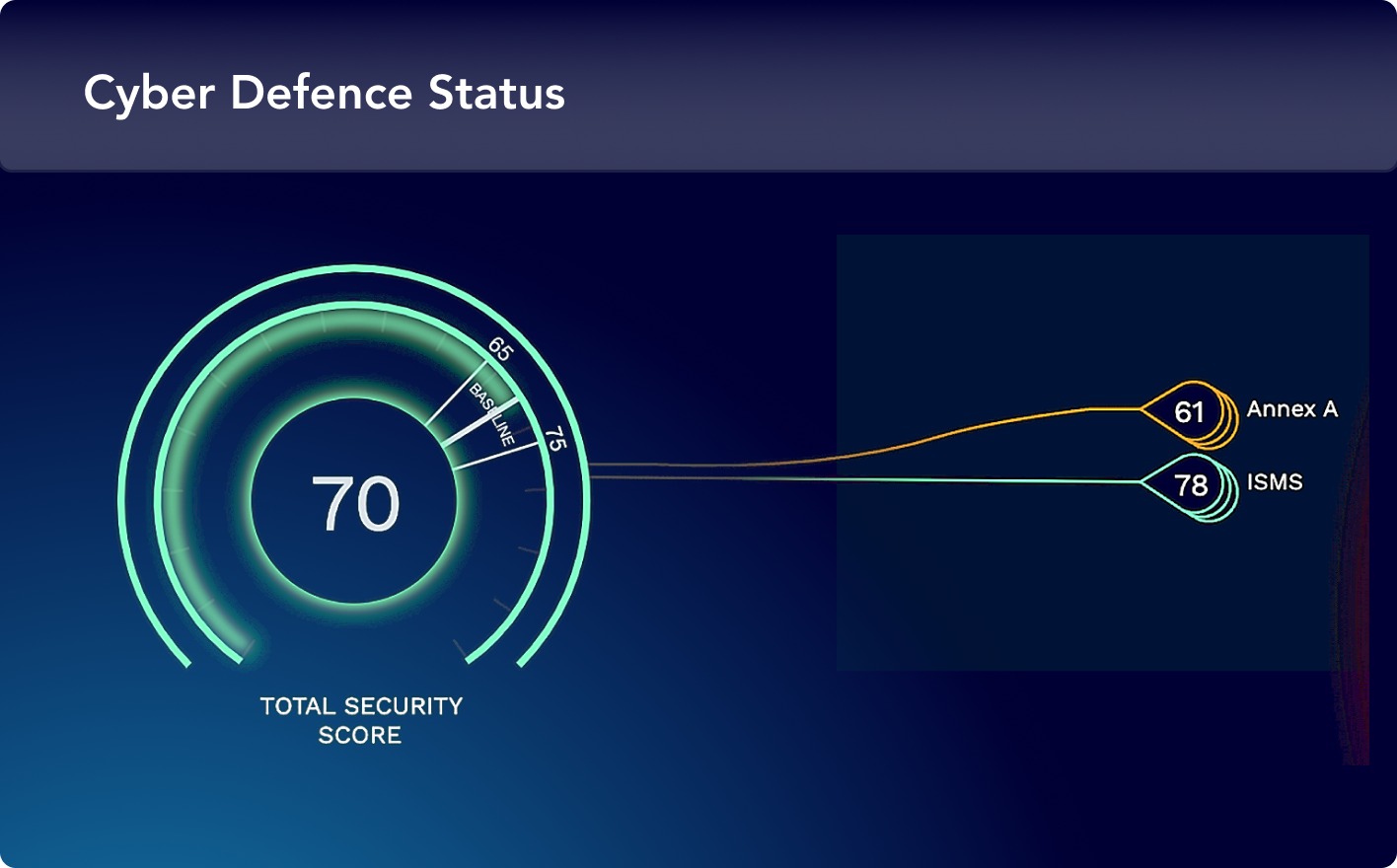
ASV, a core component of XM Cyber's comprehensive Continuous Exposure Management, empowers organizations to stay ahead of attackers, to reduce risk and improve security posture.